No matter if you love technology, hate it, or fall somewhere in between, there’s no doubt it is becoming a bigger part of your life. Our digital world is expanding as more people work from home and more companies conduct their business online. But as our digital activity increases, so does criminals’ desire to take advantage of it, leading to new advancements in computer security threats and digital crime.
In the last few years, major companies across the globe have experienced cybercrimes ranging from data breaches, to unauthorized access of financial accounts, to digital impersonations of CEOs, and everything in between. From new online stores to established corporations, companies of all types, sizes, and industries are at risk.
Although cybercriminals are continuing to become smarter and more strategic, it’s also clear that many businesses aren’t putting up much of a fight when it comes to their cybersecurity. It’s up to you to protect your organization and make sure it’s investing in its security. It’s up to us, as IT experts, to provide you with the information, resources, and services necessary to help make that happen.
3 Major Trends for Computer Security Threats in 2021
Thinking about all the new and varied cyberthreats your company faces today can quickly feel overwhelming. Where should you begin, and how can you make sure you’re staying informed?
To get started, we’ve identified 3 major trends for computer security threats in 2021 that all businesses should be aware of, so you can watch out for them in whatever form they may take.
1. Disruption
Disrupting your business is a powerful way for cybercriminals to distract you, cost you time and money, bait you into making quick and unsecure fixes, or put you at their mercy. For instance, they can use premeditated internet outages to disrupt your organization, hampering business functions and employee productivity.
Cybercriminals can also cause disruption with ransomware attacks, which have increased in popularity over recent years. In these attacks, hackers gain access to information you need, either because it is necessary to run your business or because it is sensitive information you don’t want leaked. Either way, the hackers hold your data hostage and demand you pay a ransom to get it back.
2. Distortion
With the development of technology comes the development of bots and vehicles of misinformation. This could cause more members of the public to distrust the integrity of information they encounter. Or it could cause the opposite: people might mistakenly trust false information.
In either case, it’s often bad for business. It makes it difficult to communicate with consumers or maintain their trust, especially if cybercriminals have falsified information about you or impersonated you.
Hackers are distorting the data and technologies businesses use, too. For instance, criminals who hack into your company cloud might upload fake documents that instruct employees to move money into the hackers’ account or compromise your security even further.
3. Deterioration
The deterioration of a company’s complete control over its business practices can open it up to a variety of risks, which cybercriminals are quick to take advantage of. For example, more and more businesses are implementing AI to increase their efficiency. But if you deploy untested AI, it could lead to unexpected outcomes, including higher exposure to cybercrimes.
Rapid technological advancement can also mean new federal laws to regulate it, lessening companies’ control. Many expect that increases in surveillance laws could put corporations at risk of having their information exposed. Increased privacy regulations can prevent businesses from effectively monitoring employees, making it harder to identify any insider threats.
Top 10 Computer Security Threats to Prepare for in 2021
Strengthening your cybersecurity means being proactive and staying one step ahead of cybercriminals. This starts with identifying which threats are most likely to impact companies this year.
Browse our top 3 in the infographic below, or read on for more information about all top 10 computer security threats to prepare for in 2021.
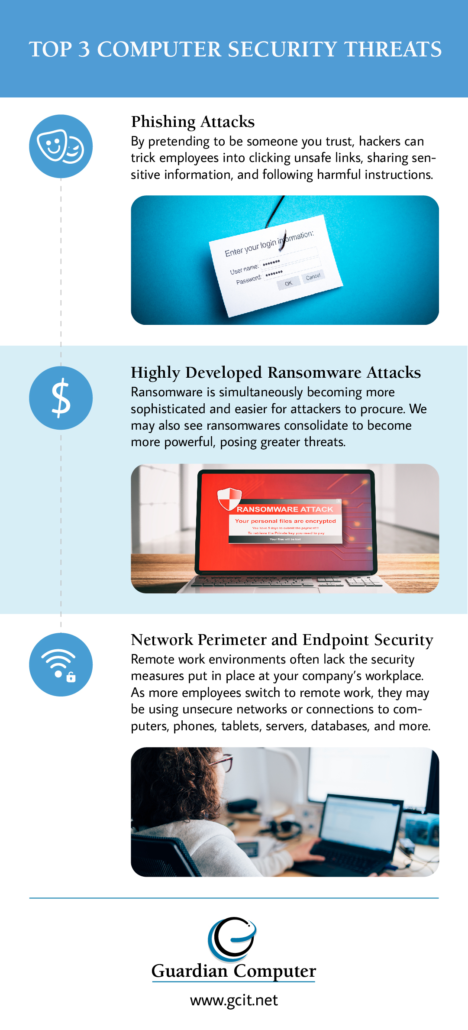
1. Phishing Attacks
In a phishing attack, a hacker pretends to be someone you trust, such as your boss or your bank. Most commonly, the hacker emails you from a familiar—but slightly altered—email address.
Typically, the hacker emails you a link or attachment. They ask you to go to a website, log into your account, or enter your personal information, such as your Social Security or bank account number. In 2019, phishing was responsible for 32% of confirmed data breaches and 78% of all cybercrimes.
This year, cybercriminals have managed to create phishing schemes through companies’ cloud applications. Because of the crime’s relative newness and the implicit trust that employees have in their companies, cloud-based phishing is one of the top cybercrimes that companies need to look out for in 2021.
2. Cloud Jacking
Cloud jacking is the process by which cloud computing is infiltrated by a third party. Once a hacker gets into your company cloud, they may try to reconfigure the cloud code to manipulate sensitive data, eavesdrop on employees and company communications, and expand their reach to take control of the entire cloud.
As we mentioned earlier, cybercriminals will also use this as an opportunity to create phishing schemes. In these scenarios, cybercriminals upload fake memos, instructions, or other files to the company cloud. Employees, believing these materials are approved by the company, download the malicious files or follow the fake instructions.
This can result in everything from workers granting hackers greater company access, to releasing sensitive data, to even moving company funds into fraudulent accounts.
3. Network Perimeter and Endpoint Security
From traveling salesmen to equity investors, professionals who work remotely can be at risk from inadequate network perimeter and endpoint security. As more and more workers have had to switch to remote work in 2021, these security issues become bigger targets for hackers.
Remote work environments often lack many of the security measures put in place at your company’s workplace. With network perimeter and endpoint security, we are referring to measures that secure your computer network and its connections to various computers, phones, tablets, servers, databases, and more.
Mobile devices, which professionals often use to conduct business on the road, are often more exposed to phishing schemes because of the ways we interact with these devices. Fast-paced communications and interactions can make people more prone to click on links, playing right into phishing schemes. Experts predict that many data breaches will occur through telecommuters, mobile devices, and off-premises assets.
Even after COVID-related restrictions lift, many workers will not be returning to company offices. In the U.S., 59% of employees working from home during the pandemic say they prefer to work remotely. Some companies have already announced they are switching to a permanent remote workforce, making adequate network perimeter and endpoint security critically important for years to come.
4. Mobile Malware
It’s not just remote employees who use mobile devices for work. Many professionals are increasingly moving from desktops to laptops or smartphones for some or all of their work.
Mobile malware is a type of software used specifically on mobile devices for malicious purposes. As larger amounts of sensitive company data are being accessed and stored on mobile devices, mobile malware attacks are very likely to be one of the most pertinent cybersecurity threats this year.
5. 5G-to-Wi-Fi Security Vulnerabilities
As cyberattacks continue to become more and more sophisticated, attacks are likely to take place in newer digital spheres. In particular, we expect to see cybercriminals exploring ways to attack the 5G-to-Wi-Fi handover.
As 5G becomes more and more commonly used, wireless providers are handing off more calls and data to Wi-Fi networks in an attempt to save bandwidth. And because of this rapid growth in 5G, the technology used to protect this handover is not yet developed enough to fully protect the transition. This gives opportunities to cybercriminals to compromise these mobile devices.
Areas that are popular for professionals to perform mobile work—such as airports, cafes, and hotels—are hotspots for the 5G-to-Wi-Fi handover. This puts the voice and data information on these mobile devices at greater risk. And while these devices have built-in technologies that allow this transition to occur quietly and without notice, researchers have already found vulnerabilities in such technologies.
6. Internet of Things (IoT) Devices
Many everyday devices, such as fitness trackers, smart security systems, and even some in-car apps, are IoT devices. Simply put, these devices are used to communicate and exchange information over a network without requiring human involvement.
For instance, your fitness tracker collects information about your health and exercise, such as your heart rate, steps taken, and calories burned. That data is sent to the cloud and processed. Under certain circumstances, that data might result in an action initiated by the technology. You might periodically receive graphs that show your fitness trends and progress, or you might be sent an alert if your heart rate is too high.
It’s not news that our world is increasingly reliant on these devices. In fact, predictions indicate that the market will grow another billion dollars by 2026. With such a major increase in new technologies, cybercriminals are likely to target IoT devices that experience security issues, as technologies in their infancy often do.
While many of the most common IoT devices are personal or smart home devices, more and more businesses are taking advantage of IoT. Smart locks, connected security cameras, smart thermostats, smart lights, voice assistants, and more are appearing in the workplace. As more company information passes through these devices, more hackers may begin targeting them.
The IoMT, or Internet of Medical Things, is a collection of medical devices and applications that can connect to healthcare IT systems using network technologies. Due to the valuable personal information available through IoMT, as well as IoMT’s unique security issues, it is especially likely that cybercriminals will target these devices.
7. Deepfakes
Deepfakes have been increasingly used against a variety of individuals and industries over the last several years. A deepfake is produced by artificial intelligence that takes an existing video, photo, or voice recording and manipulates someone’s image or voice to falsify their actions or speech. In fact, deepfakes have been popularly utilized in politics to make candidates appear to say or do something that damages their reputation.
As it relates to businesses, experts predict that deepfakes will be used by cybercriminals to impersonate members of a company to gain access to important information. These “synthetic identities” can be used to commit fraud, as hackers create fake versions of real companies to lure in unsuspecting consumers. Deepfakes can also contribute to more advanced forms of phishing, allowing hackers to more convincingly impersonate CEOs and give harmful instructions to employees.
8. Highly Developed Ransomware Attacks
Ransomware has plagued businesses for several years now. Successful attacks have caused companies to lose millions of dollars in ransom payments, encouraging hackers to keep using and refining these attacks.
According to a McAfee prediction report, the process by which attackers are able to purchase ransomware kits on the darkweb is becoming easier. Not to mention, the ransomware itself is becoming increasingly more sophisticated.
The report also predicts that ransomwares will consolidate into fewer—but more powerful—ransomwares that will work in conjunction with one another. By working together in this manner, attackers become even more capable and pose greater threats to businesses. If attacked by these ransomware powerhouses, companies may experience even greater costs from downtime and recovery.
9. Insider Threats
Insider threats, or threats posed by employees, affect 34% of businesses around the world. These employees may be acting intentionally to hurt the company or accidentally, out of ignorance or negligence. As more employees move to remote work, which opens them up to additional risks, organizations should take extra precautions to curb insider threats.
Fortunately, there are specialized tools available to combat insider threats. These tools can detect unauthorized logins, the installation of new apps on locked down computers, users with newly granted authorization access, and new devices on restricted networks. In addition, businesses should provide all employees with routine cybersecurity training to help prevent these mistakes before they’re ever made.
10. API Vulnerabilities and Breaches
An application programming interface (API) is an intermediary between applications. It determines how apps can interact with one another. APIs work behind the scenes in many everyday applications, from streaming services to social media, weather apps, instant messaging, and more.
The security used for APIs is typically less advanced than web app security. This is true for most organizations. As a result, APIs are often not made accessible to the public or outside developers.
Because so many companies are becoming more reliant on APIs, attacks on these systems—and the need for API security—should increase this year.
Protect Your Business IT with Guardian Computer
If this sounds like a full-time job—from staying informed about the latest computer security threats and cybersecurity trends, to identifying and prioritizing your business’ biggest risks, to addressing current threats and protecting against others before they ever reach your business—that’s because it is! And it’s a job our IT experts perform day in and day out, with over 100 years of combined experience in the tech solutions industry.
Guardian Computer is a full-service IT provider. Whether you need help with a single IT project or want us to fully manage your IT, we have a wide range of services to meet your every need. We also provide both in-office and remote assistance. Even if you’re across the country from our homebase in New Orleans, we’re ready to hop on a plane to meet your needs, whatever and wherever they are.
The IT solutions we offer are every bit as varied and sophisticated as the computer security threats facing business IT. To give you an idea of how we can help protect your organization, here is a small sample of our services:
- Patch enabalation and vulnerability management to keep your systems up to date and protected.
- System and SaaS backup so your data can be quickly and easily recovered in the event of a ransomware attack, natural disaster, or any other issue.
- Installation of advanced antivirus and anti-malware to keep your systems secure.
- Protection for all remotely used mobile devices with a full suite of security software, including a firewall, malware protection, and more.
- Emergency response team availability in case of a data breach.
For more information, check out our IT managed services as well as the IT solutions we offer to keep companies safe from computer security threats.
Ready to talk to someone on our team? Contact us today to learn how Guardian Computer can protect your business!







