Picture this: you’re going about your day, sipping on your favorite caffeinated beverage, when suddenly you get hit with a ransomware attack. Cue the panic and the ear-ringing stress response. It’s enough to make your head spin and your data feel like it’s held hostage. But fear not! With a proactive response plan and your personalized IT department at Guardian Computer, we’ve got your back and we’ll help you navigate through these treacherous waters.
Now, let’s get down to business. If you find yourself in the unfortunate situation of being a victim of ransomware, we’ve got a checklist that we’ll move through together.
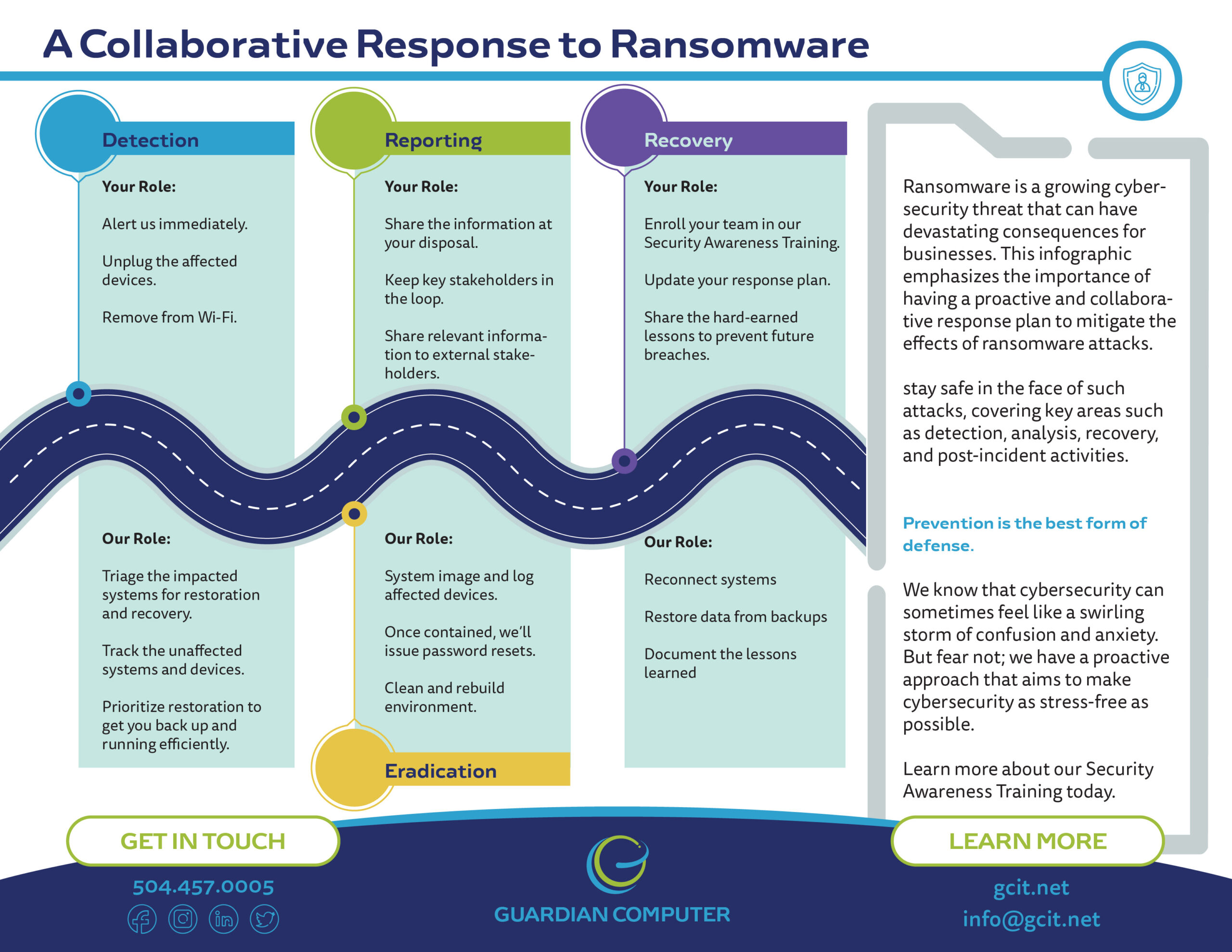
Detection and Analysis
Your job is to alert us immediately. As soon as you sound the alarm, our team will spring into action and determine which systems have been impacted and then promptly isolate them. If we see that several systems or subnets are affected, we won’t hesitate to take the network offline at the switch level.
Disconnecting individual systems during an incident may not be feasible, so we’ll prioritize isolating critical systems that are essential to your daily operations. And if taking the network offline is not immediately possible, don’t fret! You can locate the network cable and unplug the affected devices or remove them from Wi-Fi to contain the infection.
And let’s not forget about your precious cloud resources – take a snapshot of volumes to get a point in time copy for forensic investigation later.
Oh, and here’s a little secret: malicious actors may be watching your every move to see if their actions have been detected. Sneaky, right? That’s why it’s important to isolate systems in a coordinated manner and use out-of-band communication methods like phone calls to avoid tipping off these devious villains. We wouldn’t want them to make a run for it or spread ransomware far and wide before we take the networks offline.
Your next step: Power down devices if you can’t unplug them from the network. We need to stop the ransomware infection in its tracks and prevent further spread.
Our next step: We’ll triage the impacted systems for restoration and recovery. We’ll keep track of systems and devices that are untouched by the ransomware so we can prioritize their restoration and recovery. This way, we can get your organization back up and running more efficiently.
Reporting and Notification
Now, here comes your shining moment. Your role is to share all the information you have at your disposal to receive timely and relevant assistance.
Keep management and senior leaders in the loop with regular updates as the situation develops. Let key stakeholders like us, you managed security service provider, cyber insurance company, and departmental or elected leaders know what’s going on.
If the incident resulted in a data breach, make sure to follow the notification requirements outlined in your cyber incident response and communications plans. Sharing accurate and timely information internally and externally is crucial to managing the fallout.
Containment and Eradication
Leave it to us to handle the dirty work. If no initial mitigation actions seem possible, we’ll take a system image and memory capture of affected devices like workstations, servers, virtual servers, and cloud servers.
We want to collect any relevant logs, as well as samples of any suspicious malware and indicators of compromise. Then, we’ll issue password resets for all affected systems and address any vulnerabilities or gaps in security or visibility.
We’ll clean and rebuild the environment, ensuring that all malicious persistence mechanisms are removed or remediated. This could mean applying patches, upgrading software, and taking all necessary security precautions that may have been overlooked. Safety first, folks! And if customer-managed encryption keys need updating, we’ve got that covered too.
Recovery and Post-Incident Activity
We’re almost there! It’s time to reconnect systems and restore data from your offline, encrypted backups. We’ll prioritize critical services to get your business humming along smoothly again. And while we’re at it, we’ll document all the lessons learned from this incident and associated response activities.
We want to make sure we refine our organizational policies, plans, and procedures so we can be even better prepared for the next time (hopefully there won’t be one!). It’s a team effort, so your job is to share these hard-earned lessons with your team and train them to be the first line of defense against future attacks.
Security Awareness Training
We know that cybersecurity can sometimes feel like a swirling storm of confusion and anxiety. But fear not; we have a proactive approach that aims to make cybersecurity as stress-free as possible. You can sleep soundly at night knowing that we’re keeping watch of the gremlins at the gate.
Here’s the deal: the most devastating cybersecurity incidents happen due to human error. Humans tend to be the weak link in the chain. Our Security Awareness Training programs are here to save the day!
We’ll teach your employees the basics of proper security behaviors, why information security matters, how to identify social engineering attacks, the importance of setting strong passwords, using two-factor authentication, protecting physical devices, and making appropriate use of company resources. It’s like a crash course in cybersecurity superhero training! And we won’t stop there – we’ll give your team plenty of practice and revisit these topics regularly so they become second nature.
So, there you have it. A proactive and collaborative response to ransomware that will keep you safe and sound. With Guardian Computer by your side, you can conquer any cyber attack that comes your way. Stay vigilant, stay informed, and together we’ll prevail!



